- Explicit
- Scoped
- Conditional
- Cryptographically enforced server-side
Why Permissions Matter
Traditional wallet models force a tradeoff:- Either prompt users for every action, or
- Grant broad signing power with little transparency
- Apps request only what they need
- Users clearly understand what they’re approving
- Every action is checked against an approved policy before it is signed
Core Concepts
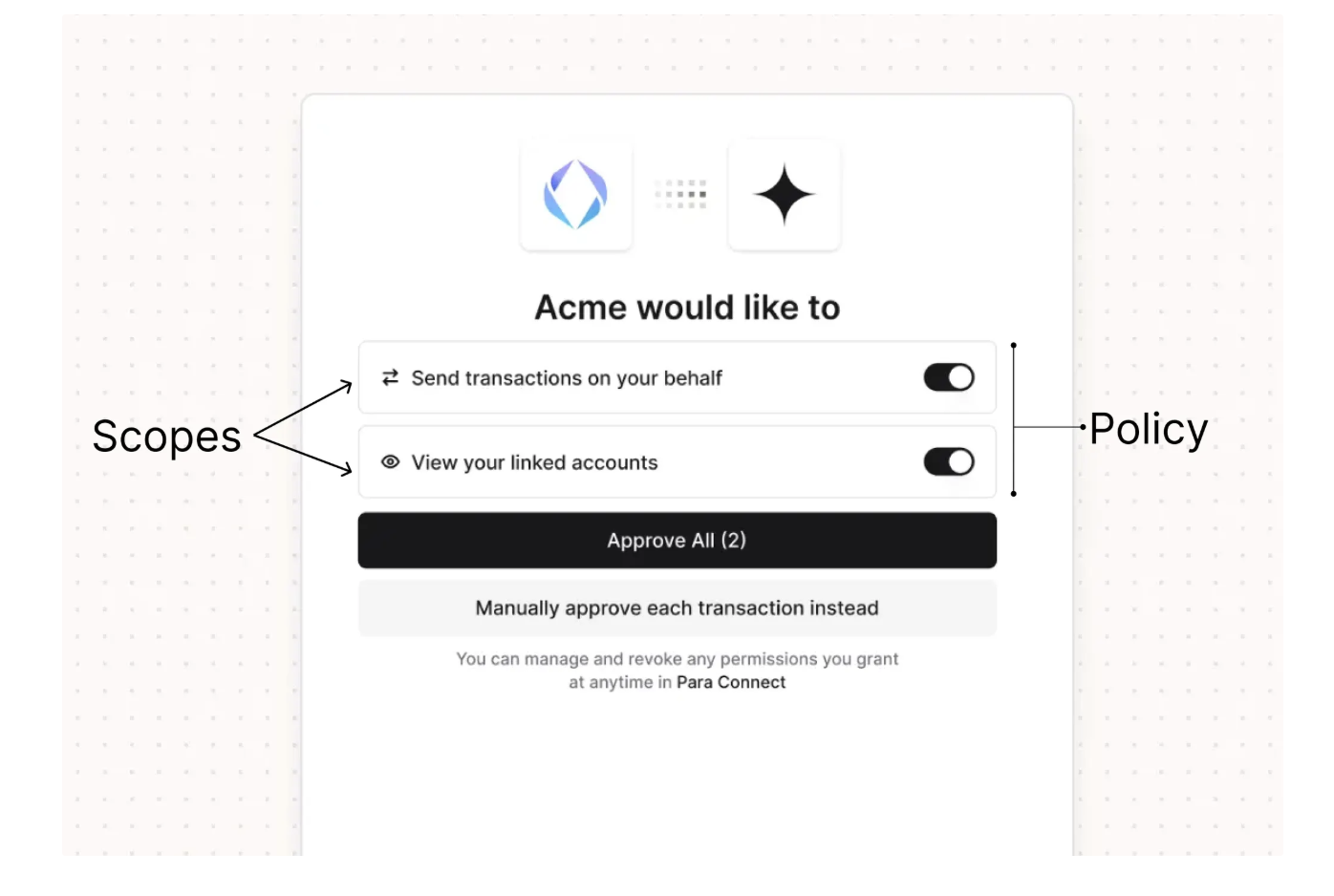
Policy
A policy defines the full set of actions your app may ever request from a user’s wallet. Think of this as your app’s permissions contract with users. If something is not included in the policy, it cannot happen. Policies are:- App-specific
- Explicit
- Immutable (changes require an updated policy version)
Scopes
Policies are broken down into scopes, which are the user-facing consent items. Each scope:- Appears as a checkbox during onboarding or login
- Groups related actions together
- Can be required or optional
- “Basic wallet actions” (required)
- “Automated transfers” (optional)
Permissions
Behind each scope are one or more permissions that describe the exact actions the app can perform, such as:- Signing messages
- Transferring value
- Calling smart contracts
- Deploying contracts
Conditions
Permissions can be constrained with conditions that define when an action is allowed. Examples:- Transfers only below a certain value
- Contract calls only to allow-listed addresses
- Actions limited to specific chains
How To Configure Policies in Para
Step 1: Define Your Policy
You start by declaring the full universe of actions your app may need:- Supported blockchains
- Types of wallet actions
- Any global time bounds (optional)
Step 2: Define Scopes
Next, you decide how permissions are grouped and presented to users. For each scope, you define:- A short, user-friendly name
- A plain-language description
- Whether it is required or optional
Step 3: Attach Permissions to Scopes
Within each scope, you specify the concrete actions that scope enables:- Message signing
- Transfers
- Contract interactions
- Deployment
Step 4: Add Conditions (Optional)
You can further restrict permissions with conditions such as:- Value limits
- Address allow-lists
- Function-level contract restrictions
What Users Experience
- The user sees clear, human-readable consent scopes
- They approve or decline each scope
- Para enforces only the approved permissions
- Any out-of-policy action is rejected before signing
Summary
Para Permissions enable the following capabilities:- You define intent once
- Users give informed consent
- Para enforces permissions every transaction
- Powerful wallet UX, without third-party control over keys